Homework Help: Questions and Answers: If antivirus, gray ware and AI scans are enabled, in what order are they performed?
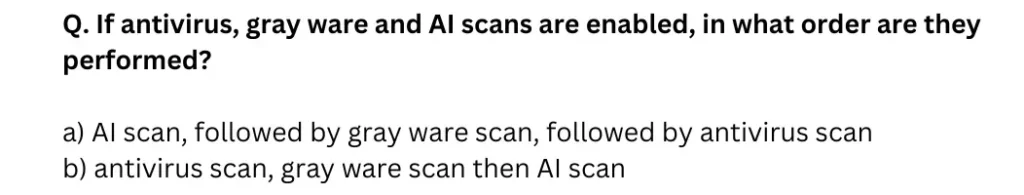
a) AI scan, followed by gray ware scan, followed by antivirus scan
b) antivirus scan, gray ware scan then AI scan
Answer:
First, we need to understand what the question is asking:
- We’re dealing with three types of scans: antivirus, grayware, and AI scans.
- We need to determine the order in which these scans are performed.
To determine the order in which antivirus, gray ware, and AI scans are performed, let’s consider the typical workflow and priorities in a scanning process:
Antivirus Scan
- Usually, antivirus scans are the first line of defense. They are designed to quickly identify and neutralize known malware and viruses. These scans are typically fast and can immediately remove or quarantine malicious software.
Gray Ware Scan
- Gray ware (also known as greyware) refers to potentially unwanted programs (PUPs) or software that is not outright malicious but can still be harmful or unwanted (like adware). After the antivirus scan clears out the obvious threats, a gray ware scan can identify and deal with these less severe, but still problematic, programs.
AI Scan
- AI scans are generally used for more in-depth analysis. They can detect sophisticated or novel threats by analyzing patterns and behaviors that traditional scans might miss. AI scans can be more resource-intensive and thorough, often running after the initial quicker scans to catch anything that was not identified earlier.
Final Answer
Based on above analysis, the correct order for performing these scans is:
- Antivirus Scan
- Gray Ware Scan
- AI Scan
Therefore, the correct answer is:
b) antivirus scan, gray ware scan then AI scan
Learn More: Homework Help
Q. In cryptography what does the term “secret” refer to?
Q. What is a top data security challenge?
Q. What is important to understand about how generative Al models work?
Q. Which prompt would be used to generate an image of a “cute kitten in a basket”?

