If you’ve recently come across the Windows Event Viewer error: A fatal error occurred while creating a TLS client credential. The internal error state is 10013.
This frustrating yet common error usually appears after system updates or changes in TLS (Transport Layer Security) settings and often affects secure connections made by apps like browsers, IIS, or network authentication protocols.
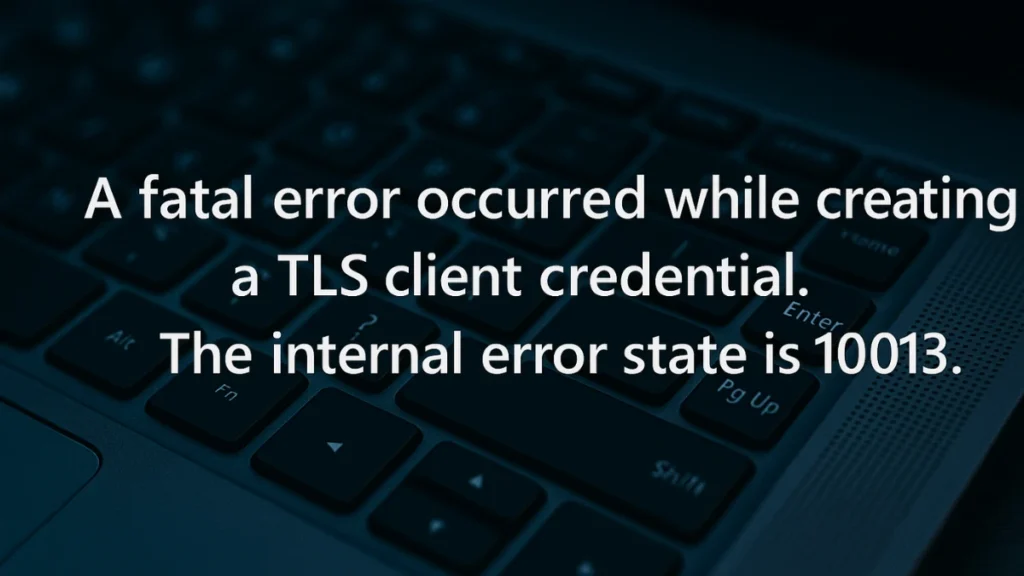
In this post, we’ll explain what the error means, real-world scenarios that trigger it, and step-by-step fixes—from basic to advanced.
Why This TLS Error Happens on Windows
The error stems from a failure to initialize a secure TLS session, usually because:
- The client and server don’t support a common TLS version or cipher suite.
- Registry settings conflict, especially around TLS versions like 1.0, 1.1, 1.2, or 1.3.
- Security accounts, certificates, or system services are misconfigured or corrupted.
- A recent Windows Update, like KB5048685, altered system behavior or permissions.
- A profile tied to an unknown or deleted user SID (e.g.,
S-1-5-32-549) is interfering.
When and Why You Might See TLS Error 10013
The TLS error 10013 usually appears in environments where system-level security configurations—particularly around TLS protocols—have been modified or tightened. It’s commonly seen after administrative changes, security updates, or when older software attempts to communicate using outdated or unsupported protocols. While the error is technical in nature, it often stems from very specific and traceable scenarios.
Here are some of the most common situations that can trigger this error:
- You force TLS 1.2 for all client devices in an enterprise environment.
- After installing cumulative Windows updates.
- IIS-hosted websites suddenly stop working with HTTPS.
- Event Viewer repeatedly logs error 10013, even though the system “seems fine.”
Top Solutions to Fix TLS Client Credential Error (10013)
Method 1: Enable All TLS Protocols in Internet Properties
- Open Internet Properties (
inetcpl.cpl) - Go to the Advanced tab
- Scroll to the Security section
- Ensure these boxes are checked:
- Use TLS 1.0
- Use TLS 1.1
- Use TLS 1.2
- Use TLS 1.3
- Click OK and restart your system
Note: TLS 1.0 and 1.1 are deprecated—only enable them if absolutely necessary.
Method 2: Update TLS Settings via Registry Editor
This ensures TLS 1.2 is properly configured:
- Press
Win + R, typeregedit, and press Enter - Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2- Create subkeys:
ClientandServer(if not already present) - In both
ClientandServer, add or update these values:Enabled→DWORD→ Value: 1 (orFFFFFFFFin hex if needed)DisabledByDefault→DWORD→ Value: 0
Tip: Some users found success only after setting Enabled = FFFFFFFF (decimal: 4294967295), not 1, especially when using Nartac’s IIS Crypto Tool, which applies this value by default.
Method 3: Update .NET Framework TLS Settings
.NET apps may fail unless explicitly told to use TLS 1.2.
Update these registry keys for both 32-bit and 64-bit versions:
HKLM\SOFTWARE\WOW6432Node\Microsoft.NETFramework\v4.0.30319HKLM\SOFTWARE\Microsoft.NETFramework\v4.0.30319
Add or update:
| Name | Type | Value |
|---|---|---|
SystemDefaultTlsVersions | DWORD | 1 |
SchUseStrongCrypto | DWORD | 1 |
Repeat for older versions like v2.0.50727 if used.
Method 4: Ensure Correct Certificate Binding (IIS-specific)
If using IIS and receiving this error while browsing:
- Open IIS Manager
- Check that your site’s HTTPS binding has a valid, non-expired certificate
- Reassign the correct SSL certificate if needed
- Restart the site
Method 5: Clean Up Registry Permissions and “Unknown Users”
This is an advanced fix for persistent errors tied to ghost user profiles:
- Open Registry Editor
- Search for the SID:
S-1-5-32-549or unknown user GUIDs - Navigate to:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileListHKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
If the unknown user is not tied to an active profile:
- Remove the user from permissions (via Advanced Security)
- Optionally delete the registry key if it’s confirmed unused
Caution: Always back up the registry before making changes.
Method 6: Reset Network and Security Stack
Open Command Prompt as Administrator and run:
ipconfig /flushdns
ipconfig /registerdns
netsh int ip reset
netsh winsock reset
netsh winhttp reset proxyReboot after running these commands.
Advanced Options (For Enterprise Users)
- Use IIS Crypto Tool to apply secure best practices.
- Create a new local administrator account to test if error is profile-specific.
- Run system integrity scans:
DISM /Online /Cleanup-Image /RestoreHealth SFC /Scannow
Can You Ignore This Error?
Yes, in many cases, this is a harmless system log that does not affect performance or app functionality. If:
- Browsers, mail clients, or internal apps still work,
- TLS errors don’t interrupt secure connections,
- And you only see it in Event Viewer…
Then it’s likely non-impactful.
To suppress it from appearing:
- Open Event Viewer
- Create a Custom View and filter out Event ID 10013
Final Thoughts
The TLS client credential error (10013) can appear after updates or configuration changes—but it doesn’t always mean something is broken. With proper registry tuning, TLS protocol alignment, and network health checks, you can resolve or safely ignore this issue.
Still stuck? Try these tools:
- IIS Crypto – Nartac Software: https://www.nartac.com/Products/IISCrypto
- Microsoft TLS Registry Documentation