Homework Help: Questions and Answers: An experienced computer technician can set up a network in 12 hours. It would take an intern 20 hours to set up the same network. If they work together, how long will it take to set up the network?
Answer:
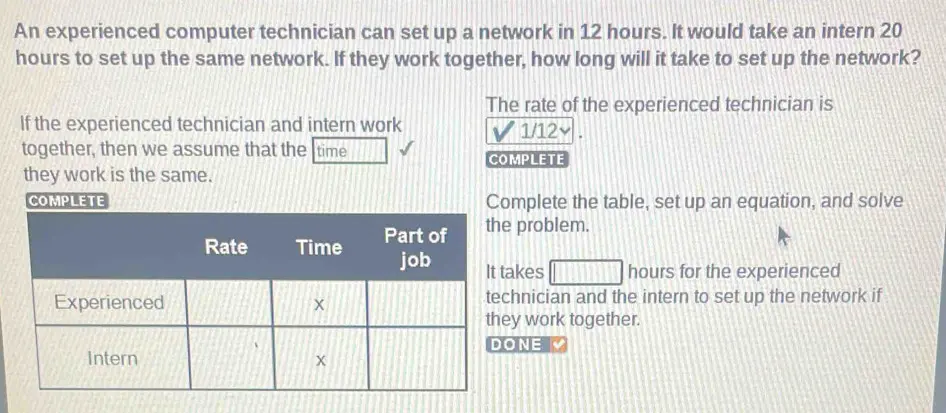
First, let’s understand the question:
NBA 2K26 – PlayStation 5
An experienced computer technician can set up a network in 12 hours, while an intern can set up the same network in 20 hours. We need to find how long it will take for to complete the job together.
Define the rates
- The rate of the experienced technician: 1/12 (This is the portion of the job completed per hour by the experienced technician).
- The rate of the intern: 1/20 (This is the portion of the job completed per hour by the intern).
Let the variable “x” represent the total time it takes for both the technician and the intern to complete the job together. Their combined rate is 1/ x.
Set up the equation
The sum of their individual rates should equal their combined rate:
1/12 + 1/20 = 1/x
To combine the fractions 1 /12 and 1/ 20, we need to find a common denominator. The least common denominator (LCD) of 12 and 20 is 60.
Convert the fractions:
1/12 = 5/60, 1/20 = 3/60
Now, add the fractions:
5/60 + 3/60 = 8/60
So, the equation becomes:
8/60 = 1/x
Now, solve for x:
x = 60/8 = 7.5
Final Answer
It will take 7.5 hours for the experienced technician and the intern to set up the network if they work together.
Learn More: Homework Help
Q. Someone who intends to gain unauthorized access to a computer system is called a:
Q. Which of the following is an effective method to learn how to avoid viruses on your computer?
Q. What could be a common cause of the “error loading ASGI” message when starting a web application?
